공급망 사이버 보안 회복력 및 위협 시뮬레이션을 위한 디지털 트윈
포괄적인 공급망 디지털 트윈 구축
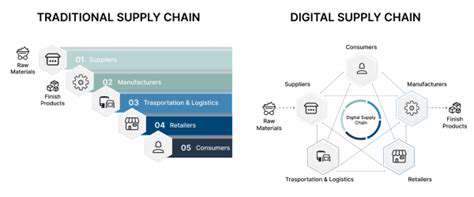
공급망의 기반 이해
견고한 공급망은 성공적인 모든 비즈니스의 중추이며, 안정적인 운영을 보장합니다.
위협 시뮬레이션 및 취약점 평가
위협 시뮬레이션
공급망의 강력한 사이버 보안 전략의 중요한 구성 요소입니다. 사이버 공격의 현실적인 시나리오를 만들고, 이를 통해
사건 대응 및 복구 개선
사건 대응에서 디지털 트윈의 역할 이해
공급망 사이버 보안 측면에서 디지털 트윈은 사건 대응에 중요한 이점을 제공합니다. 목재 가구를 애완동물 친화적으로 만드는 방법을 통해
THE END
More about 공급망 사이버 보안 회복력 및 위협 시뮬레이션을 위한 디지털 트윈
- 전원풍 목제 가구를 현대 인테리어에 어떻게 통합할까요?
- 맞춤 제작 목제 가구 제작 과정
- 인테리어 디자인에서 목제 가구와 금속 요소를 어떻게 혼합할까요?
- 클래식하면서도 현대적인 미적 감각을 위한 최고의 나무 가구
- 나무 가구로 시골 분위기를 어떻게 연출할까요?
- 나무 가구를 제대로 청소하고 관리하는 방법
- 가구에 나무를 활용하여 집 인테리어를 어떻게 통합할 수 있을까요?
- 전통 가정 스타일의 집안에 나무 가구를 어떻게 통합할까요?
- 가정 사무실용 나무 가구 선택을 위한 최고 팁
- 목제 가구가 더 지속 가능한 집을 만드는 데 어떻게 도움이 되는가
- 라이프스타일에 맞는 나무 가구를 선택하는 방법
- 거실 공간을 향상시키는 최고의 목제 가구